Enable secure application-to-application communication
I am not just a standalone application, I also need to communicate with my peers!
Yes, applications are not just standalone binaries, running on a system, sitting in some obscure room in your building, or in a faraway Cloud. Applications are designed to communicate with humans (to provide a dedicated service) as well as with each other. That’s the tricky part…
Applications communicating with applications. Really?
Think about AD authentication, SSO technology, and so on. Every software vendor wants to integrate with well-known/trendy solutions and usually does so by using APIs and/or plugins, so application-to-application is actually already used in well-identified and renowned products.
But, what about off-the-shelf software? Are they condemned to stay alone in the dark?
Once the communication protocol is established, how does a program automatically authenticate with another program?
Most of the time, this is what happens:
- Credentials to privileged access resources are stored without protection on local computers or servers
- Off-the-shelf applications use configuration files containing credentials, amongst other things
- Internal tools, i.e. applications/scripts are equipped with hard-coded credentials used in batch/cron scenarios
It seems obvious that hard-coded passwords stored locally present a risk of insider threats to IT security. While anyone can argue that these passwords are encoded in a compiled and obfuscated binary to ensure their security, it is still possible for a malicious actor to reverse the code and gain access to sensitive applications. Software applications and scripts are also easy to copy and can be reused on a third-party system. And the simple rotation of a hard-coded password is disruptive for operational activity because it means stopping operations, patching the application, and restarting operations.
So, what can be done to optimize application-to-application communication?
PAM solutions offer a dedicated feature to ensure secure and automatic authentication between applications: the Application-to-Application Password Management (AAPM).
How does AAPM work?
Privileged Access Management (PAM) solutions securely store passwords in a password vault and automatically establish sessions between systems through a session management module.
PAM market leaders also propose a mechanism to store applicative passwords in their vault so that an application wishing to communicate with another application can instantly retrieve the correct credentials automatically to do so. All it requires is to install a small agent to securely retrieve credentials from the PAM solution to provide them to the lonesome applications.
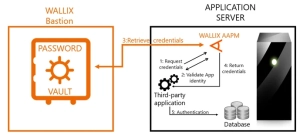
Practically, several applications such as Apache propose to integrate with external programs to provide passwords.
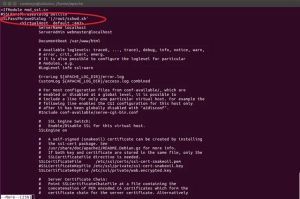
By activating this capability, it is possible to use a local agent that will securely retrieve the credentials from the PAM solution.
This type of integration is highly beneficial because it:
- Eliminates passwords from your systems
- Centralizes password management
- Provides transparent and vendor-independent connection between applications
- Offers the security advantages of a PAM solution combined with strong password management policies, password rotations, and so on.
Accordingly, your in-house programs or any off-the-shelves software are not condemned to be isolated to communicate only with humans. They can now open up to other software.
Do you want more information on how to optimize application-to-application communication? Contact our experts.


