A purpose-built cybersecurity solution for industrial control systems
Simplify Operations
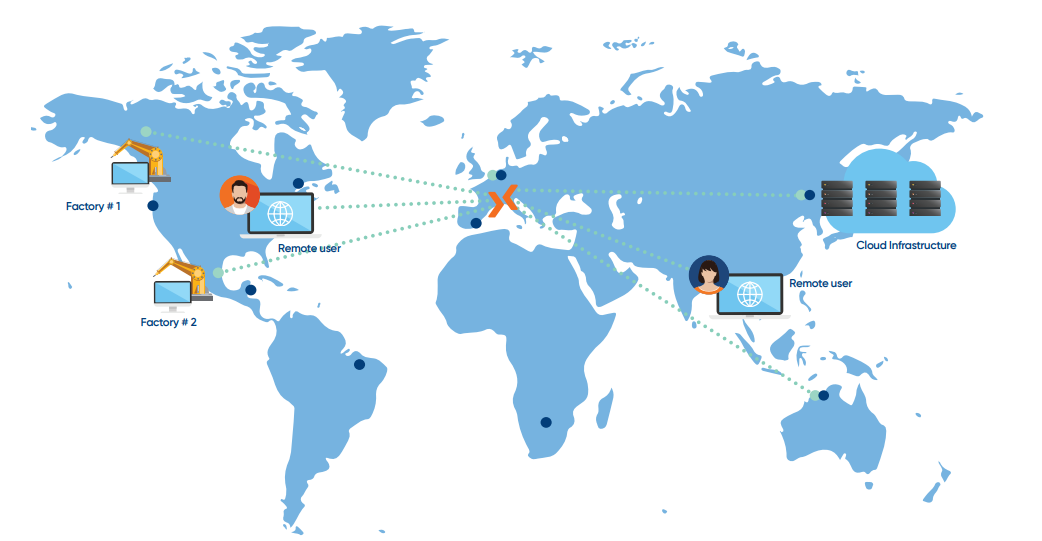
Centralize remote access using secure tunneling,
Manage session to reduce operational complexity
Streamline control across your IT & OT environment.
Increase Productivity
Enhance operational efficiency with workflows
Secures access, and promotes high adoption rates
Automate and centralize processes, freeing up resources
Address Compliance
Meet stringent regulatory standards like GDPR, NIS, ISA/IEC 62443, and NIST SP800-82 audit trails, session recording
Ensure full compliance and accountability.