-
 Infographic: Ensuring NIS Directive Security Compliance with WALLIXAUDIT & COMPLIANCE • BLOGPOST
Infographic: Ensuring NIS Directive Security Compliance with WALLIXAUDIT & COMPLIANCE • BLOGPOST -
 Privileged Access Management: Key to Compliance with the NIS/NIS2 DirectivesAUDIT & COMPLIANCE • WHITEPAPER
Privileged Access Management: Key to Compliance with the NIS/NIS2 DirectivesAUDIT & COMPLIANCE • WHITEPAPER -
 How PAM Enables IEC 62443 ImplementationAUDIT & COMPLIANCE • BLOGPOST • INDUSTRY • PRIVILEGED ACCESS MANAGEMENT
How PAM Enables IEC 62443 ImplementationAUDIT & COMPLIANCE • BLOGPOST • INDUSTRY • PRIVILEGED ACCESS MANAGEMENT -
 The CISO’s Guide to Security Compliance (with PAM)AUDIT & COMPLIANCE • BLOGPOST • PRIVILEGED ACCESS MANAGEMENT
The CISO’s Guide to Security Compliance (with PAM)AUDIT & COMPLIANCE • BLOGPOST • PRIVILEGED ACCESS MANAGEMENT -
 Ensuring Compliance with PAM: Cross-Mapping Security StandardsAUDIT & COMPLIANCE • BLOGPOST • PRIVILEGED ACCESS MANAGEMENT
Ensuring Compliance with PAM: Cross-Mapping Security StandardsAUDIT & COMPLIANCE • BLOGPOST • PRIVILEGED ACCESS MANAGEMENT
Achieve a stronger security posture during audits and minimize risks
by aligning compliance strategies with key trends:
Of corporate risk and compliance professionals said they have noticed a shift from check-the-box compliance to a more strategic approach over the past two to three years.*
Is the additional cost organizations face on average when regulatory noncompliance is a contributing factor in a data breach.**
Of security and IT leaders cited mapping controls and systems across frameworks as a method used to manage the impact of complying with multiple compliance frameworks.***
Simplified Regulatory and Compliance Frameworks
Ensuring compliance with industry regulations is critical for security, risk management, and operational resilience.
Below are key standards, frameworks, and regulations that organizations must adhere to based on their industry and operational scope.

GDPR (General Data Protection Regulation)
GDPR is a comprehensive data protection regulation that enforces strict rules on organizations handling personal data of EU citizens.
- Industry: All organizations processing personal data of EU residents, regardless of location or industry
- Key Focus: Safeguarding personal data, enforcing privacy rights, and ensuring compliance with data breach notification requirements
- Region: European Union (EU), but applies globally to any organization handling EU citizens’ data
Learn more here.
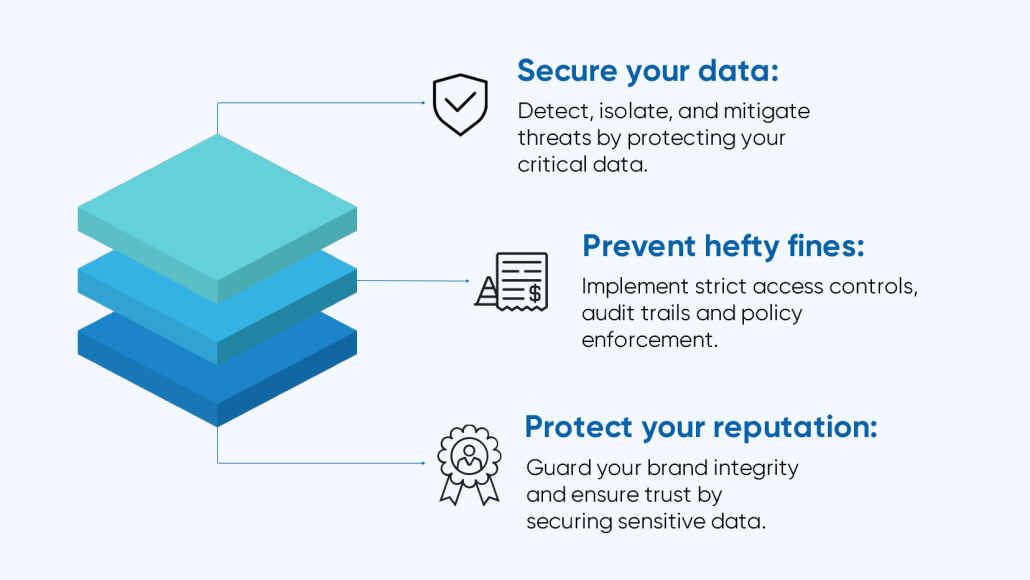
Protect your reputation, wallet, and data
Audit and Compliance Solutions
PAM
Privileged
Access
Management
Streamline IT security compliance with all-in-one access security including market-leading session management.
PEDM
Privilege Elevation
and Delegation
Management
Elevate user privileges judiciously and delegate access with precision, reinforcing your defense against potential threats.
IDaaS
Identity
as a
Service
Guarantee user identities to implement Zero Trust and ensure access security meets compliance standards.
MFA
Multi
Factor
Authentication
Ensure strong multi-factor authentication of user access to business applications and corporate assets.
IAG
Identity &
Access
Governance
Achieve better adherence to regulations, enabling meticulous risk management and streamlined auditing.
Digital Operational Resilience Act (DORA) Unpacked
Are you ready for DORA compliance?
Financial institutions face growing cybersecurity and operational risks. The Digital Operational Resilience Act (DORA) mandates a structured approach to IT risk management, resilience, and regulatory compliance.
Download our expert guide to:
✔ Understand DORA’s key requirements and impact on financial organizations
✔ Discover how Identity and Access Management (IAM) and Privileged Access Management (PAM) can help achieve compliance
✔ Learn how to enhance IT resilience and safeguard your organization from disruptions
Audit and Compliance FAQ
What is a security audit?
A security audit is an evaluation that every company handling customer data should be concerned with. They will help you identify vulnerabilities and pain points of your IT infrastructure.
What is the best way to ensure my business is complying?
Ensuring that your organization is covered against security threats is complicated. Implementing robust Privilege Identity Management (PIM) through session management will bring you a step closer towards optimizing your organization’s security.
How to solve cross-section regulations and standards with Privilege Access Management?
Reality is that all major security standards and regulations require some measure of access control. A PAM solution needs to enable both access management and session management to provide crucial assurance of controlled access and compliance in face of an audit.
Recognized by industry-leading analysts
Take the first step towards ultimate protection!
Adopt robust security measures to help you towards compliance.
Don’t wait until it’s too late! Let’s talk about it.