Understanding the Uber hack with Privileged Access Management (PAM)
Understanding the Uber hack with Privileged Access Management (PAM)
- The data of 57 million users has been stolen from Uber.
- Malicious intruders managed to gain access to a GitHub private coding site used by some Uber software engineers, find AWS credentials, and use them to steal private data.
That hurts. The number of stolen accounts is high, and most people didn’t really get what happened except that some data has been stolen from Uber one way or another. One could ask why records are on Amazon, or what is GitHub anyway? Let’s understand exactly what happened.
What led to the Uber hack?
Uber software engineer accounts on GitHub got hacked. This is the mysterious part. Did the password get stolen? Was this caused by a phishing attack?
There is not much information on this, so far.
Understanding GitHub and AWS
Amazon Web Services (AWS) is the Amazon cloud platform. Its service allows companies to offer online services and store important volumes of data. Most of the time, companies install their own software on Amazon platforms to scale their services.
This is where GitHub comes in. GitHub is an online platform dedicated to software development. It is quite popular among dev op communities because it offers source code management capabilities and distributed version control.
To keep it simple, GitHub allows for several users to work on the same code at the same time without discrepancy.
Once a part of the code is functional, it is pushed into a running platform (AWS) for testing or activation purposes.
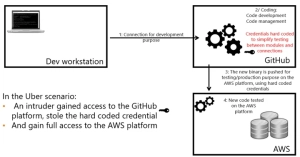
Code development can require testing hundreds of times in a day and can be dependent on already running modules, also on AWS. Accordingly, those tests rely on connections/authentications between the code in GitHub and the company environment in AWS. To simplify the testing phase and speed up the authentication process, software engineers often hard code credentials, allowing full access to AWS…
How PAM could have helped prevent the Uber hack
One would say that those are lazy engineers, who don’t respect minimum security procedures, but ask yourself:
Do you lock your front door every time you have to take your garbage out?
Again, exactly how GitHub accounts got hacked remains unclear. However, one thing is certain; there are some powerful and flexible security solutions available to provide a secure work environment and control access between two platforms without having to store credentials. Privileged access management (PAM) is one of them. PAM controls user access and activities on target systems in real-time to reduce the vulnerabilities produced by human error or negligence, and protect companies’ most valuable assets.
Specific aspects of a PAM solution would have proven valuable in the case of the Uber hack.
This is how the WALLIX PAM solution could have helped.
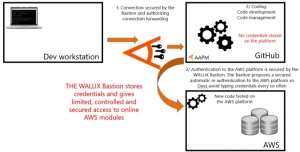
The WALLIX Bastion is designed to provide users with features specifically built to reduce insider threats linked to malicious intruders to respond to scenarios such as the one Uber fell victim of:
- Application-to-Application Password Management (AAPM), so that an application, and only the application, can connect to a server using credentials stored in the Bastion’s vault.
- The WALLIX Bastion can be used so that users never have access to the credentials used to connect to the target. The user can only access authorized resources. Any deviant behavior (bouncing to other targets or accessing unauthorized data) results in the termination of the session and in an appropriate alert.
- Another solution would be to use the WALLIX Bastion SSH agent forwarding so that developers can use their private keys stored on their own system only (as opposed to being stored in a cloud environment) to access multiple online platforms.
Do you want to know more? Give us a call or contact us here!


