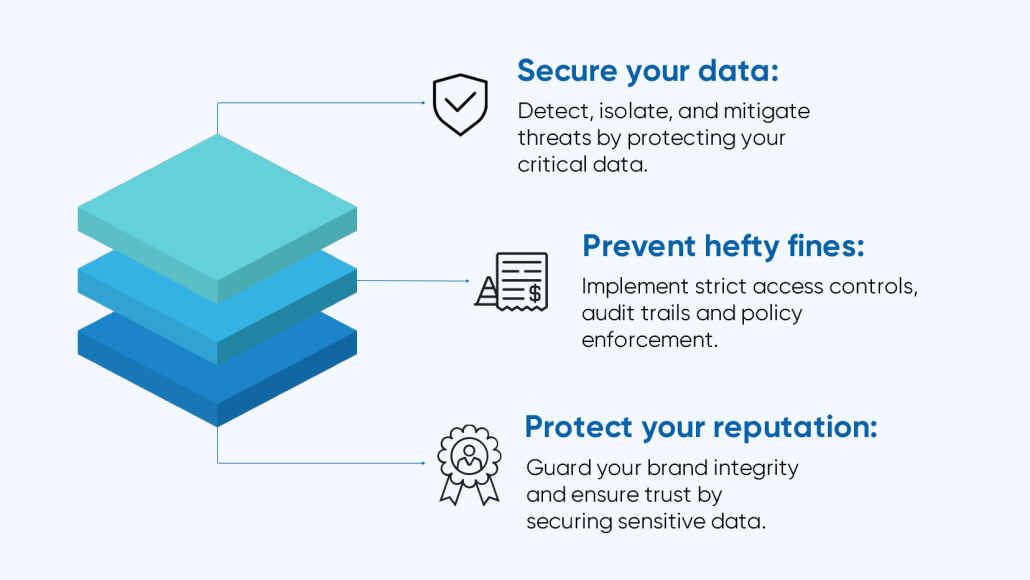
Achieve a stronger security posture during audits and minimize risks
by aligning compliance strategies with key trends:
Of corporate risk and compliance professionals said they have noticed a shift from check-the-box compliance to a more strategic approach over the past two to three years.*
Is the additional cost organizations face on average when regulatory noncompliance is a contributing factor in a data breach.**
Of security and IT leaders cited mapping controls and systems across frameworks as a method used to manage the impact of complying with multiple compliance frameworks.***