What is Zero Trust?
Understanding Zero-Trust Security
Zero Trust is a modern model of cybersecurity grounded in the “never trust, always verify” concept. Contrary to traditional security models that assume all that is within a network perimeter is secure, Zero Trust verifies all users, devices, and applications on an ongoing basis prior to granting access, no matter where they happen to be—inside or outside the corporation network.
Despite having been broadly applied in recent years, Zero Trust has its foundations in decades-old history. It was first introduced by Stephen Paul Marsh in 1994, but it gained mainstream attention only after Forrester Research’s John Kindervag popularized it in 2010. It gained more speed with significant advancements such as Google’s BeyondCorp (2009), NIST’s Zero Trust model (2018), and the U.S. government adoption in 2021.
Zero Trust is the gold standard today for defending hybrid workforces, cloud resources, and sensitive information, and it offers an active defense against modern cyber attacks like phishing, ransomware, and credential theft.
Difference between Zero-Trust Architecture (ZTA) and Zero-Trust Network Access (ZTNA)
While Zero Trust Architecture (ZTA) serves as a comprehensive security framework, applying zero-trust principles across an organization’s entire IT infrastructure, Zero Trust Network Access (ZTNA) is a specific implementation of Zero Trust focused on secure access to applications and services without exposing users to the full network.
ZTA ensures identity verification, least-privileged access, and network segmentation across all systems, whereas ZTNA enforces these principles specifically in the context of remote and cloud-based access. In other words, ZTA is the overall strategy, while ZTNA is a tactical solution within that strategy, particularly for securing external and remote access.
Why Traditional Perimeter Defenses are Insufficient
Organizations today are constructed on cloud applications, remote workers, and hybrid environments that extend far beyond the traditional network perimeter. Old security models based on firewalls and VPNs assume everything inside the network is trusted—a luxury no longer afforded.
Limitations of perimeter security
- Insider Threats & Lateral Movement: Attackers, once they’ve breached the perimeter, most commonly through stolen credentials or phishing, can laterally move throughout the network at will.
- The Perimeter is Blurred: Cloud computing, mobile devices, and remote work make it difficult to define and secure a traditional network boundary.
- Perimeter Bypass Techniques: Attackers tunnel, utilize compromised endpoints, and social engineering to bypass traditional defenses undetected.
- Maintenance Resource-Intensive: Keeping perimeter defenses up to date is a costly endeavor that struggles to keep pace with new threats, requiring regular updates, monitoring, and analysis.
- Lack of Fine-Grained Access Controls: Traditional security too often fails to enforce fine-grained access controls at the individual resource level, with unwanted users free to roam the network.
Zero Trust Network Access (ZTNA) vs. Virtual Private Networks (VPNs)
Traditional Virtual Private Networks (VPNs) were designed to provide remote users with secure access to internal networks, but they are built on an old assumption—once a user is authenticated, they are provided with broad network access. This is extremely dangerous from a security point of view, especially if credentials are compromised. On the contrary, Zero Trust Network Access (ZTNA) follows the Zero Trust paradigm in that all access requests are authenticated, device health is scrutinized, and users only access the exact resources they need—nothing more.
Unlike VPNs, which provide access to the entire network to users, ZTNA uses least-privilege access, and thus, in the event of an account being compromised, lateral movement is prevented. ZTNA is better suited for cloud environments as it offers scalability, improved performance, and real-time monitoring for proactive threat detection. ZTNA also includes device security checks, such that only compliant and secure devices are allowed access to corporate resources, while VPNs lack these security measures inherent.
As organizations embrace hybrid workforces and cloud applications, the shortcomings of VPNs become increasingly apparent. While VPNs still have their place, they require additional security controls to mitigate risk. ZTNA, on the other hand, is inherently suited to Zero Trust security architectures, delivering granular access control, continuous authentication, and improved threat visibility—making it the solution of choice for the modern enterprise.
Core Pillars of Zero Trust
Zero Trust security has five core pillars, as stated by the Cybersecurity and Infrastructure Security Agency (CISA) Zero Trust Maturity Model. These pillars operate in unison to eliminate implicit trust and subject each sphere to constant verification.
Identity Security
Validates all users, devices, and applications before granting access. This encompasses strong authentication mechanisms (such as Multi-Factor Authentication (MFA) and passwordless authentication) and behavioral analysis to detect anomalies and prevent credential-based attacks.
Device Security
Validates that all devices attempting to attach to the network are set up, compliant, and trustworthy. Organizations must maintain end-to-end device inventory, deploy endpoint security controls, and constantly check device health to minimize risks.
Network Security
Imposes network segmentation in order to limit lateral movement on the part of attackers. It entails breaking up the network into separate, stand-alone zones to ensure that only users and machines can access exactly what they’re given permission for—minimizing the blast radius of potential breaches.
Application Security
Guarantees applications execute on least privilege access rules, i.e., they have only those permissions necessary to execute. Patching, auditing, and security scans block vulnerabilities from being exploited.
Data Security
Guarantees classifying and protecting data based on sensitivity. Encryption in transit and encryption at rest, strict access policies, and continuous monitoring ensure only authorized users are able to see sensitive data—reducing exposure to data breaches.
Under these pillars, companies can transition away from legacy perimeter-based security towards a Zero-Trust model that consistently authenticates, monitors, and restricts access based on real-time risk.
Real-World Use Cases of Zero-Trust
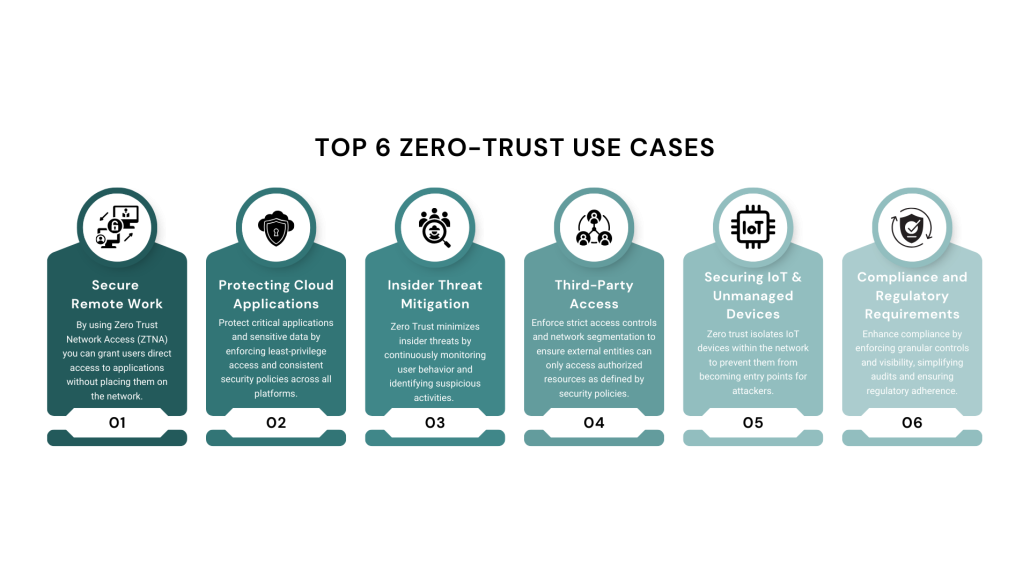
Zero Trust is more than just a concept—it’s a proven security strategy that helps organizations protect their workforce, cloud applications, third-party access, and critical infrastructure from cyber threats. Below are the top six Zero Trust use cases, illustrating how businesses can implement this security model to strengthen their cybersecurity posture.
Top 6 Zero-Trust Use Cases:
- Secure Remote Work – Ensuring secure access to corporate applications from any location.
- Protecting Cloud Applications – Enforcing consistent security policies across all platforms.
- Insider Threat Mitigation – Monitoring user behavior to detect and stop suspicious activities.
- Third-Party Access – Restricting external users to only necessary resources.
- Securing IoT & Unmanaged Devices – Preventing compromised endpoints from becoming attack vectors.
- Compliance & Regulatory Requirements – Helping organizations meet GDPR, HIPAA, and NIST standards.
By implementing Zero Trust Security, businesses can reduce risk, enhance compliance, and protect sensitive data from evolving cyber threats.
How Does Zero Trust Work?
Zero Trust is implemented through a combination of identity security, endpoint protection, network segmentation, and continuous monitoring. By aligning with CISA’s Zero Trust Maturity Model, organizations can gradually transition from traditional security to an advanced Zero Trust posture, integrating identity security at every stage.
The Zero-Trust Maturity Model (ZTMM)
The Zero Trust Maturity Model (ZTMM) is a framework designed to help organizations incrementally improve their security posture by implementing zero-trust principles. Here’s a summary of key aspects of the ZTMM:
- The ZTMM serves as a roadmap for transitioning to a zero-trust architecture, emphasizing continuous verification and strict access controls to minimize security risks.
- The Cybersecurity and Infrastructure Security Agency (CISA) released the initial version of the ZTMM in August 2021, with an updated version (ZTMM 2.0) released in March 2022.
What are the Benefits of Starting Zero Trust with Identity Security?
Starting a Zero-Trust journey with identity security ensures every access attempt is verified, reducing the risk of unauthorized access and data breaches. It also limits lateral movement by enforcing strict access controls, making it harder for attackers to navigate.
With continuous monitoring and real-time visibility, organizations can detect and respond to threats faster, preventing incidents before they escalate. Plus, identity-focused Zero Trust aligns with compliance standards, simplifying audits and regulatory requirements.
By prioritizing identity security, businesses lay a strong foundation for Zero Trust, improving protection, compliance, and overall security management.
How to Get Started
Evaluate Your Current IAM Landscape
A successful Zero-Trust strategy starts with a thorough assessment of your Identity and Access Management (IAM) infrastructure to identify vulnerabilities, outdated protocols, and security gaps that attackers could exploit. Involving IT teams and key stakeholders ensures alignment with business objectives and regulatory requirements.
Adopt Essential Identity Security Solutions
To enforce strict authentication, least privilege access, and continuous verification, organizations should implement key Zero Trust identity solutions:
- Privileged Access Management (PAM) – Centralized Control and Monitoring of Privileged Access to Sensitive Assets
- Privilege Elevation and Delegation Management (PEDM) – Eliminate administrator accounts and employ local agents on managed systems to grant specific privileges to logged-in users.
- Secure Remote Access – Provide control and governance over remote access to secure corporate IT assets and infrastructure.
- Identity as a Service (IDaaS) – Streamline the identification process, ultimately enhancing security and facilitating smoother access.
- Multi-Factor Authentication (MFA) – Strengthens user verification and prevents credential-based attacks.
- Single Sign-On (SSO) – Streamlines secure access across applications while reducing password fatigue.
- Identity and Access Governance (IAG) – Enable the implementation of security policies for managing the rights assigned to employees and contractors.
Keep in mind that Zero Trust is not a one-time setup, it requires ongoing monitoring and adaptation. By continuously tracking network activity, access behaviors, and identity risks, organizations can fine-tune security policies and stay ahead of evolving threats.
Conclusion
Zero Trust is a necessity in the evolving threat landscape. With traditional perimeter defenses no longer keeping pace, organizations must adopt a modern, identity-centric security model to protect users, devices, applications, and data.
With CISA’s Zero-Trust Maturity Model, organizations can transition from implicit trust to continuous verification and least-privilege access, making their security posture more resilient to ransomware, phishing, insider threats, and credential theft.
Beginning with identity security delivers instant risk reduction, simplified compliance, and frictionless user experience. As organizations grow their hybrid and cloud infrastructures, Zero Trust offers a scalable, proactive defense model that balances security and operational efficiency.
The transition to Zero Trust is not merely about improved security—it’s about future-proofing your organization from continuously evolving cyber threats.